Basic Cryptographic primitives used in Blockchain Notes
- In this article, we learn about the basic concept of Cryptographic primitives that are necessary to understand the fundamentals of blockchain technology.
- So we can say that Cryptographic is the heart of Blockchain technology and also need to understand the fundamental properties of the crypto primitives.
- I will try to explain some of the most important topics such as Cryptographic Hash Function, Properties of a hash function, Hash pointer and Merkle tree, Public Key Cryptography, A basic cryptocurrency.
What Is Cryptography?
- The name cryptography is derived from a Greek word called “crypto” which means “hidden” and “graphein”, “to write”. It is mainly used to protect information.
- Cryptography is the practice and study of techniques for secure communication or hidden information in the presence of third parties (called adversaries).
- It is about constructing and analyzing protocols that overcome the influence of adversaries.
- It is the Art or Science of converting plain accessible data into unclear data and again retransforming the message into its original form.
- Modern cryptography combines the disciplines of mathematics, computer science, physics, engineering, and more.
- For Example: The sender, encodes (encrypts) the readable message (plaintext) into some non-readable form (ciphertext) and transmits the ciphertext information over the network. The receiver receives the non-readable form (ciphertext) and decodes (decrypts) the ciphertext into its readable form (plaintext).
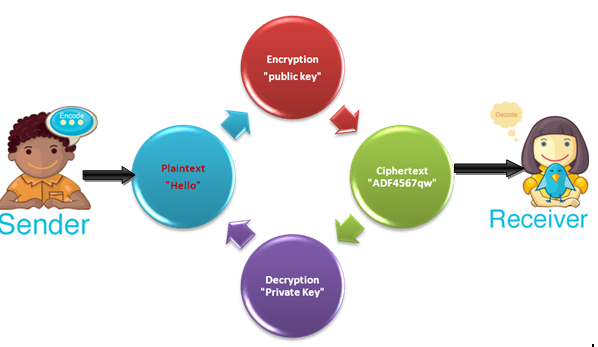
- Some important terms are defined below:
- Encryption: It is the process of Encoding normal text (plaintext) into an unreadable (ciphertext) format.
- Decryption: It is the opposite process of encryption, conversion unreadable format (ciphertext) to normal text (plaintext).
- Cipher: It is an algorithm which is used to convert readable format (plaintext) to unreadable format (ciphertext). It includes a well-defined set of operations for encryption and decryption.
- Key: Cryptography is require a key for encryption and decryption. its main work is to allows transfer the plaintext into ciphertext. so we can say that this key will help to lock and unlock the data whenever needed.
- Plaintext: Orignal (readable) form of message.
However, in the past, cryptography referred to the encryption and decryption of messages using only the secret key. Today Cryptography is classified into three different ways that are following:
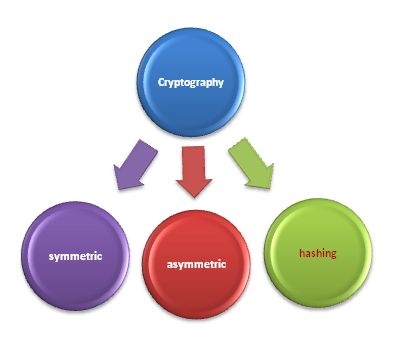
- Symmetric-key cryptography
- Asymmetric-key cryptography
- Hashing functions
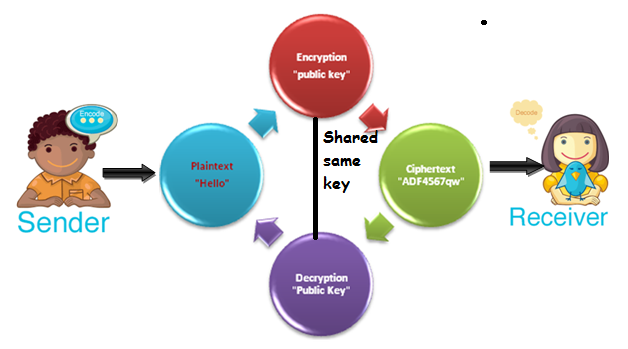
Symmetric-Key Cryptography
Same Key (secret key) is used by both parties. Sender and Receiver are used to share same key during this process. it is mainly used for privacy and confidentiality.
For Example: Using the secret key, sender encode readable form (plaintext) into some non-readable form (ciphertext) and send the ciphertext to the receiver. On the opposite side, the receiver applies shared (equivalent) key to decode the message into readable form (plain text). In this case third parties don’t know which message is send between this channel to the receiver.
Advantage
- To easy to use
- Same key for encryption and decryption
- Simpler and Faster
- Primarily used for privacy and confidentiality.
- Minimum consumption of communication resources.
Disadvantage
- Key distribution problem
- Less Secured
- Key must exchange in secure way.
- Easy for hacker to get a key as it is passed in unsecure way.
- Requires secret key sharning.
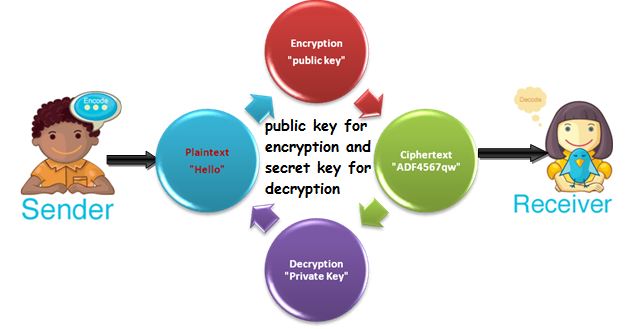
Assymetric key cryptography
It is also known as public key cryptography where uses public key for encryption and secret key (private) for decryption. This solves the key distribution problem because both parties use different key such as public key for encryption and secret key for decryption. It is mainly used for authentication, non-repudiation, and key exchange.
For Example: Here generates two different key one is a public key and scound is a private key. sender encrypts the message with receiver public key and transmits over the channel. At the receiver end, receiver decrypts the encrypted message by the private key and gets back the original message.
Advantage
- Two different keys are used names as Public and Private.
- Users get the Key from a Certificate Authority
- More Secured
- Authentication
- Primarily used for authentication, non-repudiation, and key exchange.
- No secrete sharing
Disadvantages
- Relatively Complex
- key is transferred over unsecured channels.
- Slower and not efficient.
- Longer key required
Hashing functions
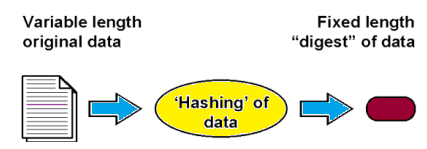
- The Hashing function is a mathematical function used in cryptography. It is a process that converts input data of arbitrary long-sized into the compressed output of a fixed-size.
- It’s easy to calculate the hash function but challenging to retrieve the original data.
- The hash value is representative of the original string of characters but is normally smaller than the original.
- Hash value, such as if there is an (accidental or intentional) change in data then it will change the hash value with a very high probability.
- Hashing functions are known as a hashing algorithm or message digest function.
Main properties of a hash function
- One-way: the digest can only be created from the message, but not vice versa.
- One-to-one: be very difficult to find two messages that create the same digest.
- Quick: it is easy to compute the hash value for any given message
- To infeasible to generate a message that has a given hash
- It is infeasible to modify a message without changing the hash
- Every minor change in the message leads to a major change in the hash value.
Application of Hashing Function
1. Password Verification
Hash functions provide protection to password storage.
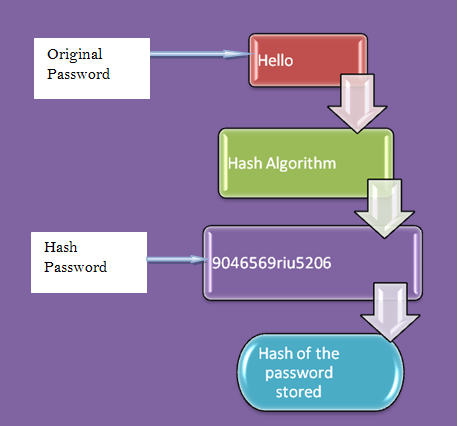
Hash-functions are sometimes used to store highly confidential data such as passwords. So it is commonly used in password verification.
For Example: When you use an online website or email account, you need a login ID and password for authentication. When you enter the password, the process starts for verification sent to the server compared to the hash values of the original server. By this process, the server will check whether the login-id is correct or not. If the login-id is correct then the platform will open for the user.
2. Data Integrity Check
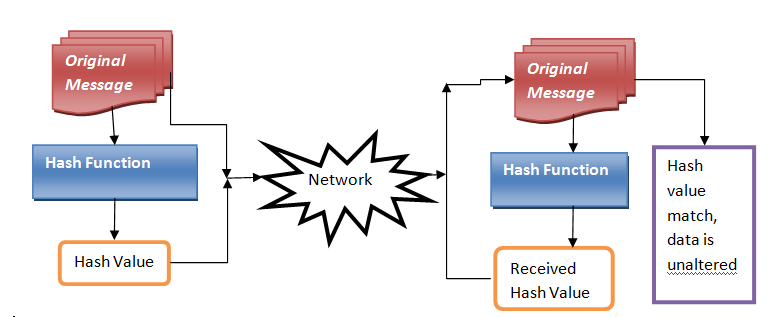
- Verifying file integrity The most obvious use is “verifying file integrity”.
- For Example: If you have just downloaded a large piece of software from a website, how do you know that you’ve received it correctly and that it has not been tampered with?
- One way is to download the file again and compare the bits: if the bits are the same, you’re probably ok, but if they’re different, which ones are the right bits?
- Finding out means yet another download with compare, and this gets very tedious very quickly. Instead, if the website publishes the hash values of its download bundles, you can check it yourself.
Read More
- Introduction of Blockchain (Notes)
- Applications of Blockchain Technology (Notes)
- How Blockchain Transaction Works? (Notes)
- Digital Signature (Notes)
- Types of Blockchain & Smart Contracts (Notes)
