GSP322- Build and Secure Networks in Google Cloud: Challenge Lab
GSP322- Build and Secure Networks in Google Cloud: Challenge Lab:
Overview
In a challenge lab you’re given a scenario and a set of tasks. Instead of following step-by-step instructions, you will use the skills learned from the labs in the quest to figure out how to complete the tasks on your own! An automated scoring system (shown on this page) will provide feedback on whether you have completed your tasks correctly.
When you take a challenge lab, you will not be taught new Google Cloud concepts. You are expected to extend your learned skills, like changing default values and reading and researching error messages to fix your own mistakes.
To score 100% you must successfully complete all tasks within the time period!
Topics tested
- Secure remote ssh access via IAP-enabled bastion
- Firewall configuration and review
Prerequisites
- Familiarity with VPC Networks
- Firewall rules and network tags
- IAP

The challenge contains 6 required tasks:
- Task 1:Check the firewall rules. Remove the overly permissive rules.
- Start the bastion host instance
- Create a firewall rule that allows SSH (tcp/22) from the IAP service and add a network tag on
bastion - Create a firewall rule that allows traffic on HTTP (tcp/80) to any address and add a network tag on
juice-shop - Create a firewall rule that allows traffic on SSH (tcp/22) from the
acme-mgmt-subnetnetwork address and add a network tag onjuice-shop - SSH to bastion host via IAP and
juice-shopviabastion
Activate Cloud Shell
| gcloud auth list gcloud config list project |
1. Check the firewall rules. Remove the overly permissive rules.
| gcloud compute firewall-rules delete open-access |
2. Navigate to Compute Engine in the Cloud Console and identify the bastion host. The instance should be stopped. Start the instance.
| gcloud compute instances start bastion –zone us-central1-b |
3. The bastion host is the one machine authorized to receive external SSH traffic. Create a firewall rule that allows SSH (tcp/22) from the IAP service. The firewall rule must be enabled for the bastion host instance using a network tag of permit-ssh-iap-ingress-ql-947 ..
| Create firewall rule to allow SSH from the IAP service |
Read Using IAP for TCP forwarding in the Google Cloud Documentation before you create the firewall rule.
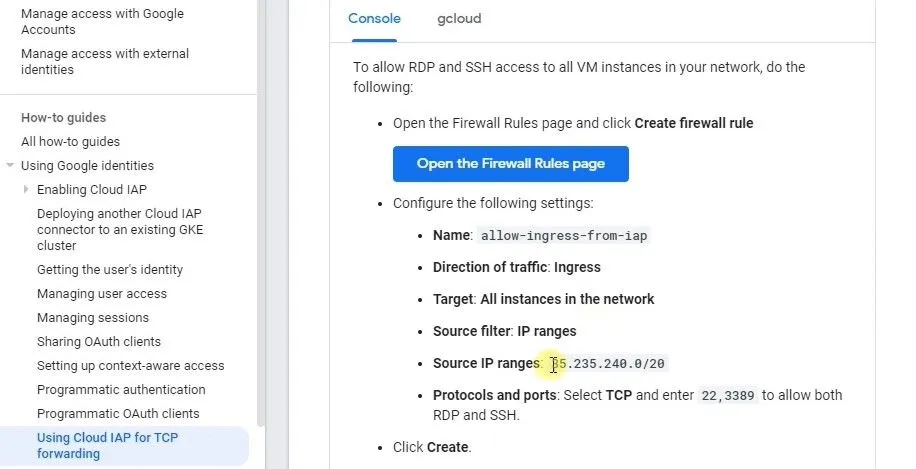
Now you have to create a firewall for bastion
- In the GCP Console go to Navigation Menu >VPC Network > Firewall.
- Click Create firewall rule.
- Configure the following settings:
Field- Value
Name- e.g. allow-ssh-from-iap
Direction of traffic- Ingress
Targets- Specified target tags
Target tags-permit-ssh-iap-ingress-ql-947
Source IP ranges- 35.235.240.0/20
Protocols and ports- Select TCP and enter 22 to allow SSH
Then Compute Engine > VM Instance > click bastion> click the Edit option
Now Add permit-ssh-iap-ingress-ql-947 to the Network tags field.
At the end of the page click Save
4. The juice-shop server serves HTTP traffic. Create a firewall rule that allows traffic on HTTP (tcp/80) to any address. The firewall rule must be enabled for the juice-shop instance using a network tag of permit-http-ingress-ql-707
- In the GCP Console go to Navigation Menu >VPC Network > Firewall.
- Click Create firewall rule.
- Configure the following settings:
Field- Value
Name- e.g. allow-http-ingress
Direction of traffic- Ingress
Targets- Specified target tags
Target tags-permit-http-ingress-ql-707
Source IP ranges-0.0.0.0/0
Protocols and ports- Select TCP and enter 80 to allow HTTP
Then Compute Engine > VM Instance > click juice-shop> click the Edit option
Now Add permit-http-ingress-ql-707
At the end of the page click Save
5. You need to connect to juice-shop from the bastion using SSH. Create a firewall rule that allows traffic on SSH (tcp/22) from acme-mgmt-subnet network address. The firewall rule must be enabled for the juice-shop instance using a network tag of permit-ssh-internal-ingress-ql-557
In this step, you have to create a firewall rule that allows traffic on SSH (tcp/22) from acme-mgmt-subnet network address.
Field- Value
Name- e.g.allow-ssh-from-mgmt-subnet
Direction of traffic- Ingress
Targets- Specified target tags
Target tags-permit-http-ingress-ql-707 , permit-ssh-internal-ingress-ql-557
Source IP ranges- IP address range of your aceme-mgmt-subnet
Protocols and ports- Select TCP and enter 22 to allow SSH.
In the Compute Engine instances page, click the SSH button for the bastion host. Once connected, SSH to juice-shop.
ssh <internal-IP-of-juice-shop> Congratulations! Done with the challenge lab.
Read
GSP342: Ensure Access & Identity in Google Cloud
Reference
